Cyber Security News Roundup – 31st July 2023
By Emily Davidson
31 July 2023
It's a new week, and that means a round up of some of the cyber security and data protection news headlines over the last 7 days! To learn more about each story, click the headings.
IBM Cost of a Data Breach Report 2023
24/7
For the 18th consecutive year, IBM released its annual Cost of a Data Breach Report last week. Built with data from over 553 breaches in 16 different countries, the report uncovers quantitative data on the consequences of a data breach. The average cost of a data breach reached an all time high in 2023, now sitting at $4.45 million, and 51% of organisations are now planning to increase security investments as a result of a breach. However, organisations that employ extensive security AI and automation experienced an average of $1.76 million lower data breach costs. Designed to cover new technologies, emerging tactics, and recent events, the report also examines the root causes, and short and long term consequences of data breaches, alongside the factors and technologies that enable organisations to limit the financial ramifications of cyber crime. You can read the full report here.
Norwegian government IT systems hacked using zero-day flaw
24/7
The ICT platform used by 12 ministries in the Norwegian Government has suffered a cyber attack, after hackers exploited a zero-day vulnerability in their third-party software. Despite the critical role of the exploited third party software in government operations, there has been no resulting disruption to work activities, with the DSS (Norwegian Security and Service Organization) stating that "It is important to stress that the government is continuing to work as normal". The DSS added that the flaw that caused the breach has now been fixed, and the agency has implemented additional security measures after handling the incident with assistance from the National Security Authority (NSM) and other security experts. As the DSS did not disclose the vulnerable software, is it unclear whether or not this is a novel attack wave that may start to affect more organisations. (Bleeping Computer)
Cyber attack affects two south England ambulance services
27/7
The South Central Ambulance Service (SCAS) and South Western Ambulance Service (SWASFT) were affected by a cyber attack that targeted third party software used by both trusts. The services, which serve a total of 12 million people, lost access to electronic patient records on the 18th July following a cyber attack on Swedish technology provider Ortivus. Whilst this did not directly affect patient care it left Ambulances unable to bring their usual levels of medical history, such as medications, allergies, and previous health incidents, which meant that any incidents were taking longer to deal with. An NHS spokesperson confirmed the cyber attack, stating that the service's "Cyber Security Operations Centre is working with affected organisations to investigate, alongside law enforcement colleagues." (BBC News)
Israel's largest oil refinery website offline after DDoS attack
30/7
Iranian hacktivist group Cyber Avengers claim to have hacked into the systems of Israel's largest oil refinery operator BAZAN Group, in an attack that rendered the company's website inaccessible from most parts of the world. The Haifa Bay-based organisation generates over $13.5 billion in annual revenue and employs more than 1,800 people, with a total refining capacity of 9.8 million tons of crude oil per year. Claiming to have breached BAZAN with an exploit targeting a Check Point firewall, the Cyber Avengers (stylised as 'CyberAv3ngers') leaked screenshots that allegedly contained BAZAN Group's SCADA systems - software applications used to monitor and operate industrial control systems - which included diagrams of "Flare Gas Recovery Unit," "Amine Regeneration" system, a petrochemical "Splitter Section," and PLC code. In a statement, a BAZAN Group spokesperson dismissed the hacktivists' claims as "false publications" and said that the circulating screenshots "have no association with Bazan or its assets." The operator also stated that the website disruption was the result of a DDoS attack, and that no damage to the company's servers or assets was observed. A Check Point spokesperson further reiterated BAZAN's findings, stressing that "none of these claims are true". (Bleeping Computer)
Attempted cyber attacks occur every second, and as we can see from the recent headlines, constantly change in nature. It's vital that your organisation is as protected as possible from all forms of cyber crime, so Contact Celerity to find out how we could protect your business!
Latest resources
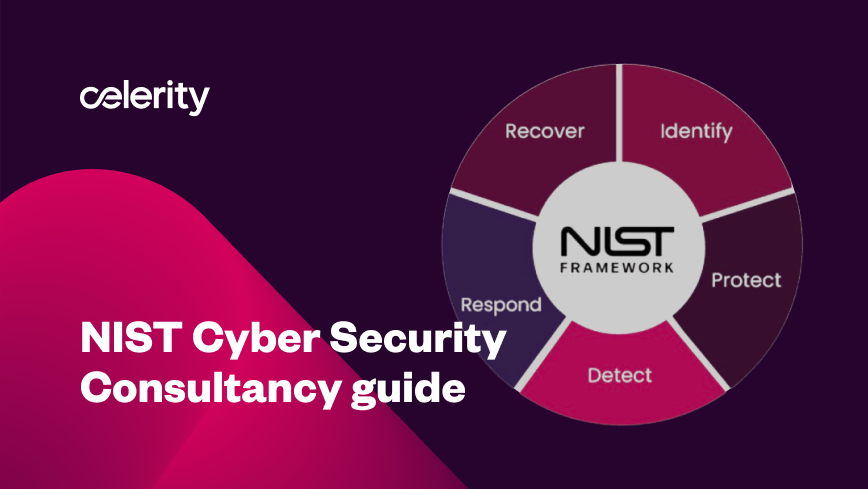
What is the NIST Cyber Security Framework?
When it comes to managing and reducing your cyber security risk, the NIST Cyber Security Framework is the most robust and accessible set of guidelines, aligning your entire organisation. The National Institute of Standards and Technology (NIST) Cyber Security Framework is made up of six essential functions to ensure businesses can manage and mitigate their […]

Quantum Computing: The Silent Threat to NHS Data Security
As NHS leaders focus on transformation priorities – shifting care from hospital to community, treatment to prevention, and analogue to digital – a silent threat looms. Quantum computing, while promising revolutionary advances in healthcare, also poses serious risks to the security of sensitive patient data. And that’s regardless of whether an organisation uses quantum or […]

What does cyber resilience actually involve?
Between 2023-2024, there were 7.78 million cybercrimes of all types committed against UK businesses alone. From ransomware to phishing attacks, the risk of a security breach is always looming. These cybercrimes can have disastrous consequences for businesses- from sensitive data breaches to complete system outages- which can come with high financial costs and reputational damage. […]