Blog
Read the latest opinion and insights from Celerity
Topics
Virtualisation
Data Security & Resilience
Managed Backup
Managed Services
Cyber Security
Utilities
Licensing
Software
Cloud & Datacentre
Hybrid Cloud
Legacy Transformation
Public Sector
Ransomware
Vulnerability Management
Storage Management
Aviation & Defence
Financial Services & Insurance
Disaster Recovery
Zero Trust

Is software asset management recommended in the ITIL?
Software asset management (SAM), where an organisation tracks its software assets throughout their entire lifecycle, is crucial to ensure software is used legally, efficiently, and compliantly with regulations. SAM focuses on helping businesses understand the terms of their software licensing, track and audit licenses to ensure compliance, and negotiate cost efficiencies with vendors.Formally known as […]
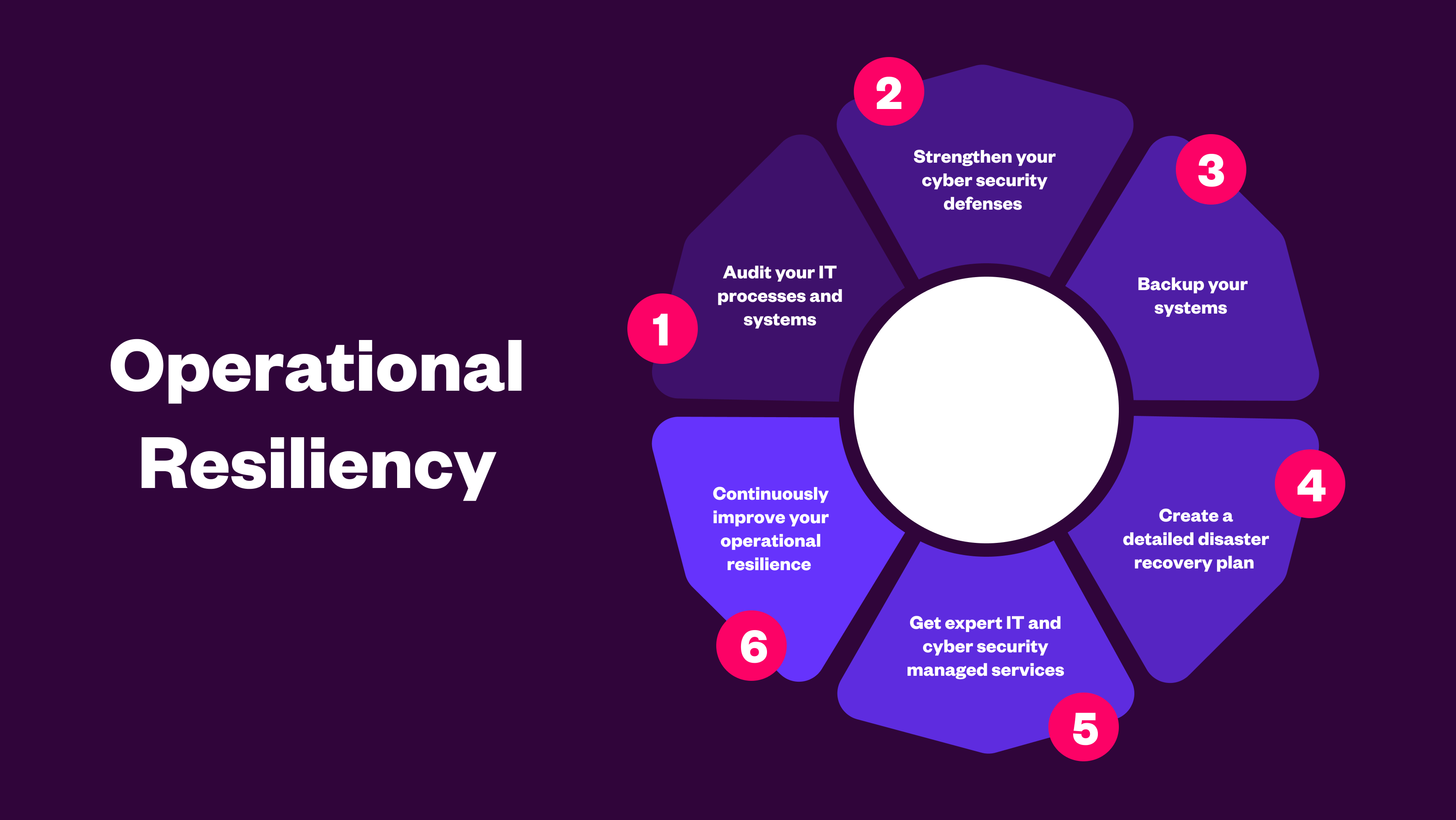
How to build operational resilience in your organisation
Operational resilience is the framework that businesses and institutions use to assess their capacity to prevent, withstand, mitigate, and recover from disruptive incidents such as cyber-attacks and IT outages. This is with the goal of reducing downtime, reputational damage, and financial impact. A misconception about operational resilience is that it’s not an essential consideration. However, […]

Five signs your business needs cyber security as a service
The importance of cyber security cannot be overstated for business continuity, protecting your reputation, and saving costs (as well as avoiding fines). It’s why 75% of businesses and 63% of charities report that cyber security is a high priority for their senior management. That’s where cyber security as a service comes into play, offering expert […]

How to find the right managed IT services first time
There are no two ways about it- selecting your IT service provider is a business-critical decision. Ultimately, you’re trusting your organisations’ cyber security, software management, data security, and IT systems over to a third party- it’s a huge decision to make. The good news? We have made this decision slightly easier for you. We’ve […]

IT security services vs cyber security managed services
These two terms can often be used interchangeably; however, the reality is there are subtle (but critical) nuances that set these services apart. It is vital that your organisation understands these differences, to ensure that you have a comprehensive approach to security that leaves no vulnerability unsecure. Half of all businesses reported some form of […]
What are the legal consequences of a data breach?
What is a Data Breach? According to the European Commission, a data breach is when ‘the data for which your company/organisation is responsible suffers a security incident resulting in a breach of confidentiality, availability or integrity’. The causes of this can vary, but ultimately it is the organisation’s responsibility to prevent this situation from arising. […]