This was a simulated attack carried out by Celerity Limited to educate users on the threats posed by Phishing.
Scroll down and follow these steps and protect yourself from future phishing scams.

What is phishing?
Phishing is an attempt to obtain sensitive information such as usernames, passwords, trade secrets, and financial information, often for malicious reasons.
Make sure you double check the emails you receive.
Although spam mail filters and security processes reduce the threat to our community, they cannot eradicate all phishing threats. The best way to avoid being a victim of a phishing scam is to know what attacks look like and report them to your retrospective security teams so the email can be eradicated
How to Detect and Handle Phishing Messages
Step 1: Identify the email as a phishing scam.
Some key indicators include:
Urgent requests. Phishing attacks attempt to induce panic in the receiver and cause the person to act before investigating the authenticity of the request.
Bad spelling or grammar. Phishing messages are notorious for containing misspelled words or poor grammar.
Mismatched email address information. Make sure the email address displayed in the from: field matches address listed in behind mailto:Generic signature line. A genuine email is usually signed with a signature, make sure it’s someone whose name you can verify, and have credible contact information.
Unexpected requests regarding personal information. Be extremely wary of following links or answering questions from contacts you did not initiate.
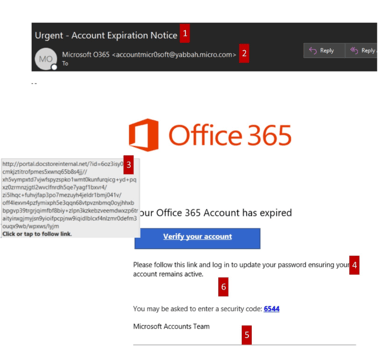
Signs of a Phish
- Phishing emails will usually contain prompt aggressive language such as URGENT, EXPIRE & LOSE.
- A display name can be spoofed very easily. Make sure you double-check the email address.
- URL links aren't always what they say they are, hover over links to see where they are taking you. This supposed Microsoft email is taking you to: http://portal.docstoreinternal.net
Step 2: Check out links and attachments before you click
Links can direct you to spoofed web pages or download harmful files on your system. You can hover the cursor over the link before you click on it to ensure that the address matches the link that was typed. You can always check the legitimacy of a message by going directly to the company or organization website or contacting them via phone.

Spoofed URL
Hover over an attachment to verify that the title matches the file type. A document that looks like it has a name “something.pdf” might actually be a file “something.exe.” An .exe extension means the attachment is actually a software program that you execute and is extremely dangerous; it can cause computer infection and data loss.
Step 3: Report and delete
If you suspect that the email is a phishing message, forward/report it to your help desk or cyber security team. After this, delete the email from your inbox.
After reading this material, we recommend closing this webpage and reviewing the phishing message that sent you to this page.
Please take note of the elements within the message that make it suspicious.

 Cyber Recovery
Cyber Recovery



